Google Nest: Exploiting DFU For Root
Posted: June 24th, 2014 | Author: cj_000 | Filed under: Nest | 8 Comments »
Nest, a company recently acquired by Google, offers a variety of popular network enabled home utilities. The most popular of which is a thermostat that allows a user to control their household temperature remotely from their smart phone. This device, although seemingly useful, if not well protected can allow an attacker the ability to remotely monitor user’s habits or network traffic. Below, we will go into a method of attacking Nest brand thermostats by leveraging the device’s DFU mode to boot unsigned code at the boot-loader level. What this means in layman’s terms is that we are able to hijack the device’s code flow very early on, allowing us to make changes without ANY restrictions. Below we will describe the attack, our method of exploiting it, and our proof of concept code which allows a user to backdoor a Nest thermostat.
The Bug:
The Nest uses a CPU similar to the OMAP3630 series. This CPU features a Device Firmware Update (DFU) mode that can be accessed by holding down the Nest’s screen while off. This mode is intended for the manufacturer to easily diagnose and repair the device. Unfortunately, in the case of the Nest, this mode also allows us to modify the device without restriction.
The Attack:
Our attack on the Nest thermostat is simple, we use the device’s recovery mode to run our own modified boot-loader (stage one and two). We then use our loaded boot-loaders to initiate a Linux kernel that is used to modify the file system on the Nest. We then add a SSH server running as root as well as functionality to create a reverse SSH tunnel to a specified host using the Nest’s virtual drive.
The Details:
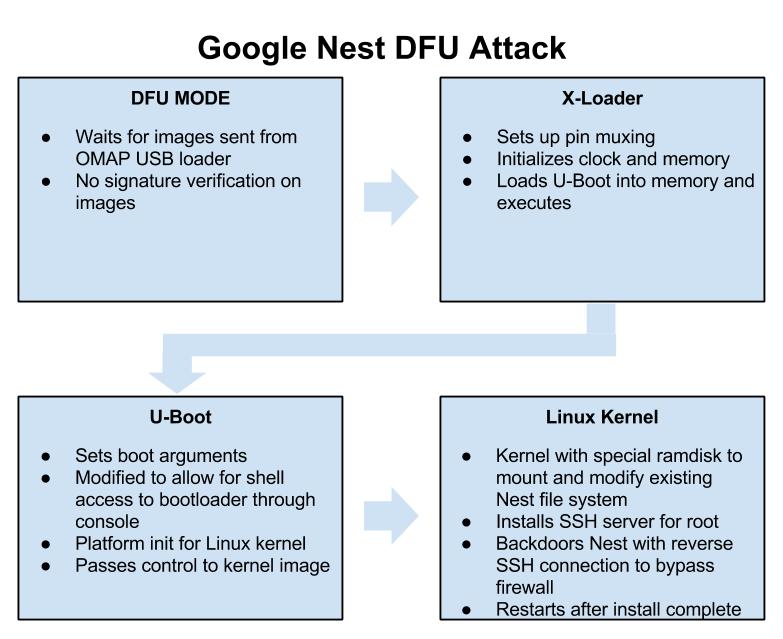
The attack is all played out within the Nest’s DFU mode which is briefly mentioned above. This mode allows a user to push a set of images and addresses to be loaded through the device’s USB port with a utility called “omap3_loader”. DFU mode is only intended as a catalyst to load the next stages of code, the first of which in our case is the x-loader binary. X-loader is a stage 1 boot-loader that is used on the Nest as the initial loading point for the system. X-loader handles getting the device ready to execute the second stage boot-loader that is responsible for loading up the Linux kernel. On the Nest, the second stage boot-loader is an open source piece of software widely used on embedded devices known as “U-Boot”. We use our own custom modified version of U-Boot that is based on the GPL released Nest version to boot a Linux kernel. This Linux kernel is only used to access the Nest’s file system and add a cross compiled SSH server called Dropbear. This allows a user to connect to their Nest and obtain root access on their thermostat. After installing the SSH server, we move on to adding a SH script which checks the Nest’s virtual disk every 10 minutes for 2 files, a “host.txt” which contains a username and host in the “username@ipaddress” format as well as a “key.txt” which contains the RSA key for the SSH connection. If these files are found, the device connects out to a remote attacker at the specified address in the “host.txt” file and makes a reverse SSH connection. This allows remote access to a user’s thermostat and home network bypassing most firewalls. This process can be stopped at any time by placing an empty file with the name “stop.txt” within the root of the Nest’s virtual USB disk.
Exploitation:
The exploit process is a single stage depending on your operating system:
- For Linux, run “NestAttack-Linux.sh”
These files push the built binaries to the Nest and handle rooting the device. This process takes less than a minute.
DEF CON:
We found this “feature” back in November 2013, and mentioned it publicly on December 5th, 2013 (see this tweet). Initially, we planned on releasing our findings at a conference this summer (along with new root methods for the Chromecast and Roku), but our talk was declined. Their loss!
We will, however, be speaking this year at DEF CON 22! Our talk, entitled Hack All The Things: 20 Devices in 45 Minutes, will feature unreleased exploits for 20 devices being released in a 45 minute period. If you are in Las Vegas this August, make sure to stop in!
Usage:
- Download package (Supports: Linux support only (more coming soon.)).
- Extract package.
- Run the appropriate attack script depending on your OS. Follow instructions after executing.
- Enjoy
Downloads:
You can get our pre-built packages for easy exploitation by using the following link.
Download NestAttack At Download.GTVHacker.com
We’re also in the process of open sourcing our build environment at:
GTVHacker GitHub – NestDFUAttack
Video:
DEF CON 22: Again, come check out our DEF CON talk this August in Las Vegas. Hack All The Things: 20 Devices in 45 Minutes, it will be awesome and there may be a special guest!

Excited about the new chromecast hack! Is it easily patched? Should we unplug our devices before the talk?
Thank you for the great work. Must have been busy fools to decline your talk.
Ciao!
I would like to see someone convert the nest into something like the BeoSound Essence. Controlling your music library with and interface like this would be absolutely awesome.
This isn’t a bug or a vulnerability. It’s a feature! If you buy a device you should be able to easily modify it.
Now that you’ve done the legwork of rooting it I can actually buy one and integrate it into my nacent home automation system without giving data about my habits to 3rd parties. Thank you!
Does the approach used on the thermostat also work on the smoke detector? I’m not about to rush off and mess around with a device designed to save my life, but just curious how similar the units are hardware-wise.
I’ve been waiting on this! Can’t wait to get to my Nest!
@BlueCop,
No need to unplug your devices from the network, we are actually going to be releasing two total root methods but I cant really say much about them. I’d keep an eye on our twitter until the conference.
@Bob,
The nest protect is completely different hardware than the thermostat and runs an RTOS. None of the GTVHacker members have audited the device yet but looked briefly into its specs to verify it wasn’t a Omap3630 device.
To everyone else, thank you for the support. Keep an eye on our twitter (@GTVHacker) for the next pre-DEFCON release. #HackAllTheThings
Can’t wait to see you guys in action again at DEFCON. I asked specifically last year about the Chromecast (and even commented on the blog :-P) so I’m very excited to see what you’ve been up to. Little bummed its not in P&T though. It’d be awesome if you could give me a shout during your talk.