Posted: May 17th, 2013 | Author: zenofex | Filed under: Asus, GTVHacker, Root | 5 Comments »
After almost 3 years of GTVHacker, we have continued to strive to bring the Google TV community the best “root” methods on the platform. To date we have released multiple methods for gaining root access on the first and second generations of devices. We’ve also released hardware roots and software roots but have yet to venture into Android application development, until now:

Let me introduce you to Cuberoot, a brand new root for the Asus Cube. This root leverages a local command execution vulnerability within a Unix socket for NFS mounting. This socket interfaces with a helper application that doesn’t properly sanitize input allowing local code execution. Luckily for us, this particular vulnerability is made better by being able to be exploited from within an Android app. “But with great power comes great responsibility”, and with such we’ve decided to not only provide the method for rooting the Asus Cube but also allow users an easy method of patching their device to prevent another application from exploiting the bug for nefarious reasons.
So, what will Cuberoot do?
Cuberoot will:
- Root your Asus Cube.
- Install SuperSu.
- Modify the Flash Player to bypass website blocks on streaming media sites.
- Disable automatic updates.
- Collect anonymous statistical information about your device.
- Allow you to patch this vulnerability, which prevents malicious applications from using this bug.
Download the app [Here] or Check out Cuberoot in action below:
UPDATE: Now in the Google Play Store!
Search for Cuberoot in the Play store, or click [Here] to install.
Posted: January 17th, 2013 | Author: zenofex | Filed under: GTVHacker, Netgear, Root | 1 Comment »

Netgear NeoTV Prime
We first broke news of the Netgear NeoTV Prime back in December, and have since been anxiously awaiting its roll out. Today the day arrived and we received our NeoTV Prime.
The NeoTV Prime uses the same form factor and hardware design as the Vizio Co-Star and Hisense Pulse. The box’s UI is a stock Google TV interface and is identical to some of the other Google TV devices.

Netgear NeoTV Prime Remote
The remote however is much different than the rest, with a smaller size and thickness plus a clickable mouse, the remote is much easier to hold and use. Although the remote is well thought out, the D-Pad leaves room for improvement. Furthermore, there does not appear to be a microphone which means the voice search additions coming with version 3 may require an additional purchase.
On to the exploits!
What would be the point of a simple first look post without some exploits!? In fact, this root method may be simpler than the method we previously disclosed for the Hisense Pulse. While the last one required ADB, this method only needs a properly set up USB drive.
Software Method:
The NeoTV Prime runs a debug service called “testmode” which checks for a USB drive with a file named “.testmode” containing the magic string “testmodemark”. The system then checks to see if the file contains the magic string “testmodemark”. If the system finds the file, it sets the “persist.radio.testmode.enabled” property to 1 and reboots. Then, if the device detects this property as 1 upon boot, it attempts to copy and then extract a file named “test_mode.tgz” from the USB drive to /tmp/. After extracting, the system tries to run a sh file named “/tmp/test_mode/test_mode.sh”. Assuming we set the permissions correctly this file will allow us to run the payload of our choosing as root.
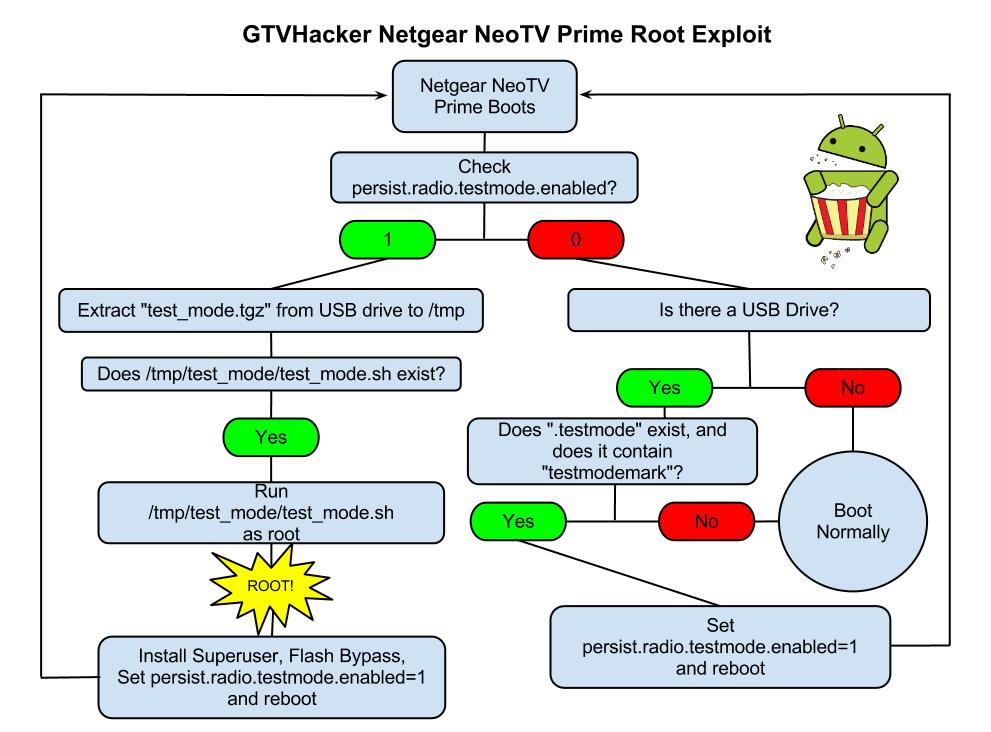
Netgear NeoTV PrimePwn Root Process
The Following are Automatically Performed:
- Installs SuperSu.apk
- Disables automatic updates
- Modifies flash plug-in to allow streaming of Hulu and other previously blocked content providers
Neo TV “PrimePwn” Root Process:
1.) Download PrimePwn.zip
2.) Extract the PrimePwn.zip to a Fat32 formatted USB drive. (test_mode.tgz, .testmode, README)
3.) Put the USB drive into your NeoTV Prime and reboot.
4.) Let the process run, it will reboot a few times and then will end at the home screen. (Approximately 3 minutes later)
5.) Remove your USB drive.
Demo Video

Netgear NeoTV Prime UART Pinout
Extra:
Netgear was kind enough to add an extra line in the init script that forces the hardware (UART) console to spawn as root. The box can be difficult to take apart and the software root is an easy process so we don’t recommend you use this method. We just wanted to mention its existence.
GTVHacker Wiki: Netgear NeoTV Prime
Enjoy!
Purchase at Amazon or Newegg
Discuss More…
Posted: December 22nd, 2012 | Author: zenofex | Filed under: GTVHacker, Hisense, Root | Tags: google, Hisense, Pulse, Root, TV | 2 Comments »
 The day has finally arrived, the Hisense Pulse has launched and is finally in our hands. Upon first look we were impressed with the speed of navigation from within the menus. If you have experience with the previous generation of the Google TV platform then you’ll recognize the Pulse’s UI which seems to be almost identical to that of the Logitech Revue. The form factor of the Pulse is similar in size and shape to that of the already released Vizio Co-Star, and the motherboard layout makes it seem like they used a similar design. One difference between the Co-Star and the Pulse is that the Pulse’s remote is much more intuitive and its use feels more natural. All together it’s exactly what someone would expect for another device in the Google TV family but with one of the cheapest prices in its generation.
The day has finally arrived, the Hisense Pulse has launched and is finally in our hands. Upon first look we were impressed with the speed of navigation from within the menus. If you have experience with the previous generation of the Google TV platform then you’ll recognize the Pulse’s UI which seems to be almost identical to that of the Logitech Revue. The form factor of the Pulse is similar in size and shape to that of the already released Vizio Co-Star, and the motherboard layout makes it seem like they used a similar design. One difference between the Co-Star and the Pulse is that the Pulse’s remote is much more intuitive and its use feels more natural. All together it’s exactly what someone would expect for another device in the Google TV family but with one of the cheapest prices in its generation.
Our biggest and most unexpected surprise came within moments of our first examination of the Pulse. Upon receiving any new hardware, partially because of our previous experience with the Revue, we like to start off disassembling the hardware even before powering on a device. After doing so in this particular instance we found that a hardware root-shell is enabled by default through the serial console header on the device’s motherboard. Better yet, the root-shell is available in both recovery and normal boot which allows for tinkering of the device in both modes of operation.  While we’ve seen serial consoles left in prior Google TV devices (see: Logitech Revue), we had yet to see a Google TV device that included a shell within both normal and recovery mode, let alone one in the second generation of the Google TV platform. While leaving a hardware shell leaves the box almost completely vulnerable its use still requires some soldering experience. However, after further exploration we noticed a 4 pin header on the Pulse PCB which allowed us to simply plug in a common connector and avoid soldering all together! This adapter is conveniently in a location that can be accessed by either temporarily opening the device and plugging in the adapter, or for more permanent use, by cutting a hole in the side of the case. The ease of access to the pin header as well as the obvious oversight of the serial console was just the beginning of our findings.
While we’ve seen serial consoles left in prior Google TV devices (see: Logitech Revue), we had yet to see a Google TV device that included a shell within both normal and recovery mode, let alone one in the second generation of the Google TV platform. While leaving a hardware shell leaves the box almost completely vulnerable its use still requires some soldering experience. However, after further exploration we noticed a 4 pin header on the Pulse PCB which allowed us to simply plug in a common connector and avoid soldering all together! This adapter is conveniently in a location that can be accessed by either temporarily opening the device and plugging in the adapter, or for more permanent use, by cutting a hole in the side of the case. The ease of access to the pin header as well as the obvious oversight of the serial console was just the beginning of our findings.
After finishing up our quick analysis of the hardware we finally had the opportunity to explore how the device’s software side was configured. We found that even with the hardware root oversight being as unexpected and less secure than any of its counter parts, the software side was worse. After browsing through the system’s init scripts, and checking the props, we noticed that a simple “adb root” to the device would restart adb as root therefore providing us with a root shell via adb.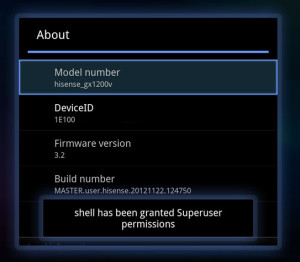
Why is this device so much less secure than any of the other Google TV devices? Is this an oversight, or did someone at Hisense purposely leave it there to show community support? We hope that someone did this purposely as it would be great if a manufacturer or Google finally embraced the modding community, but it was probably just an oversight.
Knowing this, we thought it would be best to release our findings for the community as soon as possible as it will likely be patched quickly with the next automatic update. However, if you do have a Hisense Pulse and would like to take advantage of root before it’s possibly patched. We have a package that will perform a few community desired modifications such as:
- Install Superuser.apk and su binary to device.
- Patch flash player to allow content to be played from previously blocked websites (Hulu, Fox, CBS, NBC, etc.).
- Disable automatic updates to preserve root (can easily be reversed).
You can find information on our modification package at the GTVHacker Wiki page for the Hisense Pulse
We have more coming soon, check back around the first of the year for a sneak peek at something even more awesome than this!
Looking to purchase a Hisense Pulse and also want to support GTVHacker? [Use this link to purchase at Amazon]
Discuss More…
Posted: February 26th, 2012 | Author: zenofex | Filed under: GTVHacker, Root, Sony, Updates | Comments Off on Rumor: New update coming in Monday patching Sony GoogleTV exploit
A source has told us that Sony has already started testing a fix for the recent exploit and plans to have it coming out as soon as Monday as an OTA update. If this is correct that means that after you receive this automatic over-the-air update you will no longer be able to run the “recovery downgrade” or perform the recovery exploit to root your Sony GoogleTV. We advise all users to perform the recovery downgrade as well as the software root as soon as possible. The current custom kernel included in the root works very well and there are more custom kernels coming soon! If anything, the main reason to perform the exploit is to preserve your box from receiving the next update (which from what we’ve heard is only a security update). Then you will still have the option to revert back to the normal OTA at anytime. You will also however have the option to run one of our new upcoming kernels which we guarantee will make you all very happy. Otherwise, if you haven’t already performed our root, and your box does take this automatic update you will be stuck with using only official Sony GoogleTV builds, no Hulu/content provider bypass and no root.
As we’ve stated in the previous post, the guide and information about the process can be found at our wiki. Also just a note, the guide below states that you need 4 thumb drives to accomplish the exploit but with a little more work you are able to accomplish the entire process with 1.
How to Root Guide:
GTVHacker.com: Running Unsigned Kernels On Sony GTV
For a more detailed look into how the exploit and recovery downgrade works, check out the about:
GTVHacker.com: About The Sony Downgrade & Rebooter (Root)
And finally, for support or to comment checkout our forum post:
GTVHacker Forums: NSX-GT1 and NSZ-GT1 exploit to run unsigned kernels!
GTVHacker
Posted: February 7th, 2011 | Author: resno | Filed under: Logitech Revue, Root | Tags: GTVHacker, logitech, revue, software root | 4 Comments »
It has been a few short weeks since we released the hardware root on the Logitech Reuve and the community has really sprung up in support of the progress we have made. Almost immediately, people began requesting root for non-virgin boxes,(Passed the initial setup phase) and which did not require opening it to solder onto the board.
Although we remain committed to reaching the overall goal of opening the Revue up to the masses, our best efforts have still not resulted in what we all want, the elusive ROOT.
It took a team of people countless hours… literally countless hours to make the progress that has been made, and we realize there is more work to be done. Rest assured, we are trying most every avenue available to us, and once we have made progress we will release it to the world! Keep your eye on gtvhacker for the latest in developments.
Do you have a Revue? If so, did you hear about root in time to use it?
Posted: January 31st, 2011 | Author: resno | Filed under: Logitech Revue, Root | Tags: BreakVue, googletv, GTVHacker, live wallpapers | Comments Off on Live wallpapers on GoogleTV?
 With the hardware root under our belt, we have been able to try a few other things. Here’s one cool thing thats been reported so far, Live Wallpapers! If you have an Android phone, you know them well. They are essentially wallpapers with different animations.
With the hardware root under our belt, we have been able to try a few other things. Here’s one cool thing thats been reported so far, Live Wallpapers! If you have an Android phone, you know them well. They are essentially wallpapers with different animations.
Have you been able to do anything on your rooted GoogleTV?









 With the hardware root under our belt, we have been able to try a few other things. Here’s one cool thing thats been reported so far, Live Wallpapers! If you have an Android phone, you know them well. They are essentially wallpapers with different animations.
With the hardware root under our belt, we have been able to try a few other things. Here’s one cool thing thats been reported so far, Live Wallpapers! If you have an Android phone, you know them well. They are essentially wallpapers with different animations.